CryptoLocker Virus removal: Victims urged to report to FBI, not pay ransom
US-CERT has issued a warning to businesses and consumers of the dangerous CryptoVirus ransomware, urging victims to not give in to the hackers' demands and instead report it to the FBI's Internet Crime Complaint Center.
The warning also said that some victims have paid the attackers and did not receive the promised decryption key. It also said: "If one computer on a network becomes infected, mapped network drives could also become infected,"
The new CryptoLocker Virus malware has been infecting computers via the Internet since October.
The malicious malware, which infects computers using Windows PCs via fake UPS or FedEx tracking notification emails, holds every file on a user's computer ransom until they pay the hacker's demands.
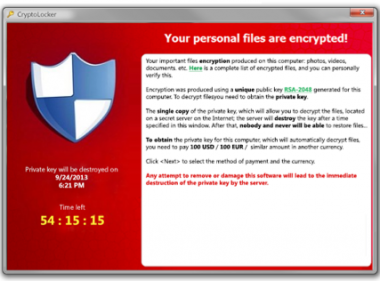
The files are cryptographically locked, making users unable to access them. The hacker demands $100 in bitcoins within 100 hours. A ticking clock counts down, showing the time limit that the user has to fulfill the demands.
The CryptoLocker virus spreads when the fake UPS emails are opened. The file installs itself in the "Documents and Settings" folder, scans the hard drive and locks files associated with Microsoft Word and Adobe Photoshop. A pop-up window with the countdown then pops up, along with details on how to pay the ransom.
If users give in to the hacker's demands and pay the ransom, a key is given to decrypt the files. However, if the ransom is not paid within the 100 hours, the files cannot be restored and are lost.
CryptoLocker reportedly uses a domain generation algorithm giving the malware up to 1,000 possible domain names from which to connect to its command and control infrastructure, according to Costin Raiu, director of the Global Research and Analysis Team at Kaspersky Lab. He added that the encryption that CryptoLocker uses is currently uncrackable as it uses a solid encryption scheme.
The CryptoLocker is one of the dangerous types of malware, known as "ransomware." If the ransom is paid, the hackers claim to restore and decrypt the files, and return access to the hard drive.
So far, there is no security protection for this virus and users must be wary of opening any suspicious 'legitimate'-looking emails.
Good anti-virus software can remove the virus from your computer but unfortunately cannot undo the damage that has already been up. The best advice to protect all your files is to repeatedly back-up your computer, especially irreplaceable family photos and important documents.











